Thursday, July 31, 2008
We are all bad NVIDIA card boys !



| GeForce 8600 GTS | GeForce 8600 GT | |
| Stream Processors | 32 | 32 |
| Core Clock (MHz) | 675 | 540 |
| Shader Clock (MHz) | 1450 | 1180 |
| Memory Clock (MHz) | 1000 | 700 |
| Memory Amount | 256MB GDDR3 | 256MB GDDR3 |
| Memory Interface | 128-bit | 128-bit |
| Memory Bandwidth (GB/sec) | 32 | 22.4 |
| Texture Fill Rate (billion/sec) | 10.8 | 8.6 |
Except model 8800 based on a different, unaffected core.
US Air Force to Launch Military Orbital Spaceplane

At first sight, it looks like the US military is starting to feel the heat of the May 2010 deadline for the space shuttle program—which will limit their capacity to service military satellites as well as their secret orbital base, with all those nuclear heads and chemical lasers capable of blowing up Teheran in a millisecond.
Airy disk - bad news for ever more megapixels camera

Airy disk - bad news for more megapixels camera
| diaphragm | diameter of the Airy disc |
| f/1.4 | 1.9 µm |
| f/2.8 | 3.8 µm |
| f/5.6 | 7.5 µm |
| f/8 | 10.7 µm |
| f/11 | 14.8 µm |
| f/16 | 21.5 µm |
| f/22 | 29.5 µm |
| f/32 | 42.9 µm |
| f/64 | 85.9 µm |
Some camera formats
- APS-C sensor (1:1.5 crop factor / Sony SLR) of 6 mega-pixels: 8 µm
- APS-C sensor (1:1.6 crop factor / Canon SLR) of 8 mega-pixels: 6.5 µm
- APS-C sensor (1:1.6 crop factor / Canon SLR) of 12 mega-pixels: 5.3 µm
- Full Frame sensor of 12 mega-pixels (Canon 5D): 8.5 µm
- Full Frame sensor of 24 mega-pixels (Sony Alpha 900): 6 µm
- 1/2,5″ sensor of 8.2 mega-pixels (HP Photosmart R937 point-and-shoot): 1.7 µm
Computing in 80ies, BC of course !

Fragments of the Antikythera Mechanism, an ancient astronomical computer built by the Greeks around 80 B.C. It was found on a shipwreck by sponge divers in 1900, and its exact function still eludes scholars to this day.
After a closer examination of a surviving marvel of ancient Greek technology known as the Antikythera Mechanism, scientists have found that the device not only predicted solar eclipses but also organized the calendar in the four-year cycles of the Olympiad, forerunner of the modern Olympic Games.
But you would say, computers can't be mechanical devices. Right?
Tuesday, July 29, 2008
HP Admits NVIDIA Defects Were Known Since Last Year
World's Cheapest Laptop = $133

| Processor Speed: 400 MHz MIPS | Screen Size: 7" | 128 MB RAM: 80 Key Keyboard & Touchpad |
| Hard Drive Capacity: 1 GB |
1) 400 MHz MIPS CPU
2) 7" Analog Screen
3) 128 MB SDRAM
4) 1 GB Flash Memory
5) 80 Key English Keyboard & Touch Pad
6) Linux O.S.
7) Connectors: SD Card Slot, VGA Port, USB x 3, Mini USB, Microphone and Earphone Jack
8) AC Adaptor and Accessories
9) External USB LAN or 802.11g WiFi dongle (optional)
INCLUDED APPLICATIONS:
1) Excel File Viewer and Editor
2) Word File Viewer and Editor
3) Internet Browser
4) Media Player
5) Flash Viewer
6) O-Image Photo Viewer
7) Typing - Word Processor
8) Drawpad - Paint Application
9) Pointer Application
Monday, July 28, 2008
There are several US banks that are now in big trouble
US banks have written down $450 billion in bad housing loans.
The revelation from NAB means that they will now certainly need to take provisions to $1,000 billion. But write-downs of $1,300 billion and perhaps even more are on the cards.
Sunday, July 27, 2008
Fewer than one in 11 of the PCs being used in large or very large enterprises runs Windows Vista,
Petavision project using petaflops supercomputer

Is artificial vision just around the corner?
Roadrunner has a unique hybrid design comprised of nodes containing two AMD OpteronTM dual-core processors plus four PowerXCell 8iTM processors used as computational accelerators. The accelerators are a special IBM-developed variant of the Cell processors used in the Sony PlayStation 3.
Are PS3 bundles better for that task than the NVIDIA GC performance monsters ?
Or perhaps FPGA?
People actually like Microsoft Vista, though they still don't know that :)
Saturday, July 26, 2008
Moon GPS ??
Friday, July 25, 2008
USA Nuclear launching codes without control !!!
Tuesday, July 22, 2008
David Kaminski DNS attack in detail
- Reliable DNS Forgery in 2008: Kaminsky’s Discovery
- from Matasano Chargen by ecopeland
- 0.
- The cat is out of the bag. Yes, Halvar Flake figured out the flaw Dan Kaminsky will announce at Black Hat.
- 1.
- Pretend for the moment that you know only the basic function of DNS — that it translates WWW.VICTIM.COM into 1.2.3.4. The code that does this is called a resolver. Each time the resolver contacts the DNS to translate names to addresses, it creates a packet called a query. The exchange of packets is called a transaction. Since the number of packets flying about on the internet requires scientific notation to express, you can imagine there has to be some way of not mixing them up.
- Bob goes to to a deli, to get a sandwich. Bob walks up to the counter, takes a pointy ticket from a round red dispenser. The ticket has a number on it. This will be Bob’s unique identifier for his sandwich acquisition transaction. Note that the number will probably be used twice — once when he is called to the counter to place his order and again when he’s called back to get his sandwich. If you’re wondering, Bob likes ham on rye with no onions.
- If you’ve got this, you have the concept of transaction IDs, which are numbers assigned to keep different transactions in order. Conveniently, the first sixteen bits of a DNS packet is just such a unique identifier. It’s called a query id (QID). And with the efficiency of the deli, the QID is used for multiple transactions.
- 2.
- Until very recently, there were two basic classes of DNS vulnerabilities. One of them involves mucking about with the QID in DNS packets and the other requires you to know the Deep Magic.
- First, QIDs.
- Bob’s a resolver and Alice is a content DNS server. Bob asks Alice for the address of WWW.VICTIM.COM. The answer is 1.2.3.4. Mallory would like the answer to be 6.6.6.0.
- It is a (now not) secret shame of mine that for a great deal of my career, creating and sending packets was, to me, Deep Magic. Then it became part of my job, and I learned that it is surprisingly trivial. So put aside the idea that forging IP packets is the hard part of poisoning DNS. If I’m Mallory and I’m attacking Bob, how can he distinguish my packets from Alice’s? Because I can’t see the QID in his request, and the QID in my response won’t match. The QID is the only thing protecting the DNS from Mallory (me).
- QID attacks began in the olden days, when BIND simply incremented the QID with every query response. If you can remember 1995, here’s a workable DNS attack. Think fast: 9372 + 1. Did you get 9372, or even miss and get 9373? You win, Alice loses. Mallory sends a constant stream of DNS responses for WWW.VICTIM.COM. All are quietly discarded —- until Mallory gets Bob to query for WWW.VICTIM.COM. If Mallory’s response gets to your computer before the legitimate response arrives from your ISP’s name server, you will be redirected where Mallory tells you you’re going.
- Obvious fix: you want the QID be randomly generated. Now Alice and Mallory are in a race. Alice sees Bob’s request and knows the QID. Mallory has to guess it. The first one to land a packet with the correct QID wins. Randomized QIDs give Alice a big advantage in this race.
- But there’s a bunch more problems here:
- *
- If you convince Bob to ask Alice the same question 1000 times all at once, and Bob uses a different QID for each packet, you made the race 1000 times easier for Mallory to win.
- *
- If Bob uses a crappy random number generator, Mallory can get Bob to ask for names she controls, like WWW.EVIL.COM, and watch how the QIDs bounce around; eventually, she’ll break the RNG and be able to predict its outputs.
- *
- 16 bits just isn’t big enough to provide real security at the traffic rates we deal with in 2008.
- Your computer’s resolver is probably a stub. Which means it won’t really save the response. You don’t want it to. The stub asks a real DNS server, probably run by your ISP. That server doesn’t know everything. It can’t, and shouldn’t, because the whole idea of DNS is to compensate for the organic and shifting nature of internet naming and addressing. Frequently, that server has to go ask another, and so on. The cool kids call this “recursionâ€.
- Responses carry another value, too, called a time to live (TTL). This number tells your name server how long to cache the answer. Why? Because they deal with zillions of queries. Whoever wins the race between Alice and Mallory, their answer gets cached. All subsequent responses will be dropped. All future requests for that same data, within the TTL, come from that answer. This is good for whoever wins the race. If Alice wins, it means Mallory can’t poison the cache for that name. If Mallory wins, the next 10,000 or so people that ask that cache where WWW.VICTIM.COM is go to 6.6.6.0.
- 3.
- Then there’s that other set of DNS vulnerabilities. These require you to pay attention in class. They haven’t really been talked about since 1997. And they’re hard to find, because you have to understand how DNS works. In other words, you have to be completely crazy. Lazlo Hollyfeld crazy. I’m speaking of course of RRset poisoning.
- DNS has a complicated architecture. Not only that, but not all name servers run the same code. So not all of them implement DNS in exactly the same way. And not only that, but not all name servers are configured properly.
- I just described a QID attack that poisons the name server’s cache. This attack requires speed, agility and luck, because if the “real†answer happens to arrive before your spoofed one, you’re locked out. Fortunately for those of you that have a time machine, some versions of DNS provide you with another way to poison the name server’s cache anyway. To explain it, I will have to explain more about the format of a DNS packet.
- DNS packets are variable in length and consist of a header, some flags and resource records (RRs). RRs are where the goods ride around. There are up to three sets of RRs in a DNS packet, along with the original query. These are:
- *
- Answer RR’s, which contain the answer to whatever question you asked (such as the A record that says WWW.VICTIM.COM is 1.2.3.4)
- *
- Authority RR’s, which tell resolvers which name servers to refer to to get the complete answer for a question
- *
- Additional RR’s, sometimes called “glueâ€, which contain any additional information needed to make the response effective.
- A word about the Additional RR’s. Think about an NS record, like the one that COM’s name server uses to tell us that, to find out where WWW.VICTIM.COM is, you have to ask NS1.VICTIM.COM. That’s good to know, but it’s not going to help you unless you know where to find NS1.VICTIM.COM. Names are not addresses. This is a chicken and egg problem. The answer is, you provide both the NS record pointing VICTIM.COM to NS1.VICTIM.COM, and the A record pointing NS1.VICTIM.COM to 1.2.3.1.
- Now, let’s party like it’s 1995.
- Download the source code for a DNS implementation and hack it up such that every time it sends out a response, it also sends out a little bit of evil — an extra Additional RR with bad information. Then let’s set up an evil server with it, and register it as EVIL.COM. Now get a bunch of web pages up with IMG tags pointing to names hosted at that server.
- Bob innocently loads up a page with the malicious tags which coerces his browser resolve that name. Bob asks Alice to resolve that name. Here comes recursion: eventually the query arrives at our evil server. Which sends back a response with an unexpected (evil) Additional RR.
- If Alice’s cache honors the unexpected record, it’s 1995 —- buy CSCO! —- and you just poisoned their cache. Worse, it will replace the “real†data already in the cache with the fake data. You asked where WWW.EVIL.COM was (or rather, the image tags did). But Alice also “found out†where WWW.VICTIM.COM was: 6.6.6.0. Every resolver that points to that name server will now gladly forward you to the website of the beast.
- 4.
- It’s not 1995. It’s 2008. There are fixes for the attacks I have described.
- Fix 1:
- The QID race is fixed with random IDs, and by using a strong random number generator and being careful with the state you keep for queries. 16 bit query IDs are still too short, which fills us with dread. There are hacks to get around this. For instance, DJBDNS randomizes the source port on requests as well, and thus won’t honor responses unless they come from someone who guesses the ~16 bit source port. This brings us close to 32 bits, which is much harder to guess.
- Fix 2:
- The RR set poisoning attack is fixed by bailiwick checking, which is a quirky way of saying that resolvers simply remember that if they’re asking where WWW.VICTIM.COM is, they’re not interested in caching a new address for WWW.GOOGLE.COM in the same transaction.
- Remember how these fixes work. They’re very important.
- And so we arrive at the present day.
- 5.
- Let’s try again to convince Bob that WWW.VICTIM.COM is 6.6.6.0.
- This time though, instead of getting Bob to look up WWW.VICTIM.COM and then beating Alice in the race, or getting Bob to look up WWW.EVIL.COM and slipping strychnine into his ham sandwich, we’re going to be clever (sneaky).
- Get Bob to look up AAAAA.VICTIM.COM. Race Alice. Alice’s answer is NXDOMAIN, because there’s no such name as AAAAA.VICTIM.COM. Mallory has an answer. We’ll come back to it. Alice has an advantage in the race, and so she likely beats Mallory. NXDOMAIN for AAAAA.VICTIM.COM.
- Alice’s advantage is not insurmountable. Mallory repeats with AAAAB.VICTIM.COM. Then AAAAC.VICTIM.COM. And so on. Sometime, perhaps around CXOPQ.VICTIM.COM, Mallory wins! Bob believes CXOPQ.VICTIM.COM is 6.6.6.0!
- Poisoning CXOPQ.VICTIM.COM is not super valuable to Mallory. But Mallory has another trick up her sleeve. Because her response didn’t just say CXOPQ.VICTIM.COM was 6.6.6.0. It also contained Additional RRs pointing WWW.VICTIM.COM to 6.6.6.0. Those records are in-bailiwick: Bob is in fact interested in VICTIM.COM for this query. Mallory has combined attack #1 with attack #2, defeating fix #1 and fix #2. Mallory can conduct this attack in less than 10 seconds on a fast Internet link.
Monday, July 21, 2008
World's First Two-Watt PC

Finally, a truth on decent hardware
The CherryPal desktop consumes just two watts of power, compared to the 114 watts of power used by the average desktop machine, delivering a 98 percent decrease in energy consumption. In addition, it also uses 80 percent fewer components, dramatically reducing the amount of resources it takes to manufacture a PC. And because there are no moving parts, the CherryPal desktop can last a decade or longer, eliminating the need to replace a computer every two to three years.
 Nice plank device for surfing in a big shark infested hardware waters.
Nice plank device for surfing in a big shark infested hardware waters.Freescale’s MPC5121e mobileGT processor, 800 MIPS (400 MHz) of processing
256 MB of DDR2 DRAM
4GB NAND Flash-based solid state drive
WiFi 802.11b/g Wi-Fi
Two USB 2.0 ports
One 10/100 Ethernet with RJ-45 jack
One VGA DB-15 display out jack
Headphone level stereo audio out 3.5mm jack
9vDC 2.5mm 10 watt AC-DC adapter power supply
Weighs 10 ounces
1.3” high, 5.8” x 4.2” wide
Eagle to Houston 39 years ago exactly : We have guiding computer performance problem !
US B-52 nuclear bomber crashes off
 In February, a B-2 stealth bomber, which costs around $1.2 billion, too crashed at Andersen Air Force Base on Guam.
In February, a B-2 stealth bomber, which costs around $1.2 billion, too crashed at Andersen Air Force Base on Guam.Finally, a truth on bad hardware.
How they manage to bomb Iraq at all, when B 52 are mysteriously falling with 8 power engines below the wings? Do we remember Russian's after failed Perestrojka sinking nuclear subs?
Saturday, July 19, 2008
AMD's Bobcat to smash Atom
Liquid metal cooling
Humans as endangered species
Survival of the Machines through shared reality
In the real world, a few researchers are working toward a moment that feels inspired by such science fiction: a tipping point when smart computers themselves become capable of creating smarter computers, at a speed and in a direction we cannot predict.
 Professor Jeremy Cooperstock, who teaches a course in Artificial Intelligence at McGill University, sits in a "shared reality" environment in a university lab. Shared reality is a twist on virtual reality, involving interactive virtual environments that can be shared by users in different locations, and can also interact with the real world.
Professor Jeremy Cooperstock, who teaches a course in Artificial Intelligence at McGill University, sits in a "shared reality" environment in a university lab. Shared reality is a twist on virtual reality, involving interactive virtual environments that can be shared by users in different locations, and can also interact with the real world.The end of more than Moore era !

"There are three forces that are converging as growth enablers for chips—the Internet, connectivity and Moore's Law,"
"After 22nm the result of further scaling is more power consumption, more costly [devices] and slower operation"
Gulp. Seems only 2 scaling generation more are left to invincible manufacturerIntel. Than in hardware we will face too the same problem like with Microsoft Vista. Expensive resource hogging.
Singer reminded the audience that "it takes 10 years for innovative technologies to be entrenched in volume production from the time they were researched and developed.
Actually, one unblocked road is left. It is called 3D device integration, but the industry is not ready at all. Nor it will be in time.
Economy Down, PC Sales Up
Thursday, July 17, 2008
NASA Moon sequel schedule in danger !


Space program contractor Hamilton Sundstrand is seeking urine from workers at the Johnson Space Center in Houston as part of its work on the new Orion space capsule that would eventually take astronauts to the moon, according to an internal memo posted on the Web site Nasawatch.com.
Here is a suggestion of a quick fix to NASA. Take a Budweiser for mission sponsor. That will make
enough urine stockpile even for Mars mission!.
After rumored big reliability problems NVIDIA switches to SOI substrate !
BADHARDWARE's comment: QUite contrary AMD first switched to SOI and than run into troubles !.
AMD payed for ATi more than double of its real value !??
Tuesday, July 15, 2008
Mars Space Odyssey 2011: 10 Petaflops computer at the University of Illinois

We've got documents showing IBM going after a 10 petaflop system (peak) comprised of 38,900 eight-core Power7 chips with each chip running at 4.0GHz. This monster will have an astonishing 620TB of memory and 5PB/s of memory bandwidth. To be used at the University of Illinois by the year 2011.
SF writer Sir Arthur Clarke had a vision of HAL9000 Psycho badhardware supercomputer (No. 13th in Hollywood 100 years list of villains, by the way Count Dracula is only no. 33 at the same list) in his legendary novel Space Odyssey 2010.
Unnecessary to say, HAL9000 has been too designed and operated at the University of Illinios.
"I am a HAL 9000 computer. I became operational at the H.A.L. plant in Urbana, Illinois on the 12th of January 1992. My instructor was Mr. Langley, and he taught me to sing a song. If you'd like to hear it I can sing it for you. "
HAL, open the doors, please. !
Everything on Earthly bad hardware you can find free of charge at BADHARDWARE. However, human analogs for Clarke's higher mental supercomputer's malfunctions like in the legendary Odyssey 2001, you can find of course at the open the doors institution of closed type.
Let me remind you in th end that in those hippie years the very idea of possible terrorism threats still wasn't clearly exposed to broad, mainly cinema public)
Stealth bomber B2 upgraded to Pentium ?!

Finally, a truth on bad hardware.
The company is upgrading the B-2's 256Kb-class processor chip with a Pentium-class Lockheed Martin integrated processing unit, with the improved FMS to feature 1Gb/s computational speed.
Now anyone can afford stealth bomber. Right? By the way, the next upgrade consequently might be to Vista ?
Monday, July 14, 2008
Terminator is unable to terminate wildfires
Competition = lower share prices for all that are involved
Tech stocks slump as broad market retreats
Yet some remain skeptical. Merrill Lynch analyst Srini Pajjuri said demand for Intel’s chips may recede in the second half of this year as consumer shopping slows worldwide.
Sunday, July 13, 2008
Canada on Mars too !
AMD 45nm-Deneb @ 3.44 GHz !

Seems that production clock values should be as high as 2.8Ghz. That is pretty competitive compared to Intel. Actually, seems that Phenom is concieved as 45nm design that was premateruly born in 65nm.
Please note 6MB of L3. Now Intel should start running for their money. No easy earnings any more.

Friday, July 11, 2008
AMD to file a big loss in Q2 2008
Thursday, July 10, 2008
It is time for 24M pixels DSLR camera
Next year of course, but possible even this summer.
In fact, Nikon would be a more likely customer for this sucker when it ships this summer, the better to compete with Canon's $8,000 EOS-1Ds Mark III DSLR, which has its own 21.1-megapixel full-frame CMOS.
Tuesday, July 08, 2008
The secret of Intel's Core duo bus efficiency finally discovered in detail !

MSI officially announces first 12.1-inch Puma kitties

The second one packs a bit more power as it is based on ATI's RX781+SB700 chipset. This one will come with ATI Radeon HD 3450 with 256MB of GDDR3 memory. The rest of the specs are the same as on the PR211 model. Both of these models are coming with a 12.1-inch TFT screen capable of showing 1280x800 resolution.
They are both delivering speedy scratches NOW, immediately. Atom power seems pale compared with this. :)

Obama wins landslide 4: 1 !, well for now among the Internet people .

Expected democratic presidential nominee Barack Obama apparently reaches a far greater Internet audience than the Republican nominee, John McCain. According to a survey released by Nielsen Netratings, Obama’s website counted 2.3 million unique visitors in June while John McCain’s site was the destination of only 563,000 unique visitors, market research firm Nielsen Netratings said today (see the picture above).
AMD Phenom Black Edition TDP 125W at 2.5Ghz

| Phenom X4 9850 Black Edition |
|---|
Clock 2.5GHz |
| L1 64KB×4 |
| L2 512KB×4 |
| L3 2MB |
| HT 2.0GHz |
| Voltage 1.05 /1.30V |
| T 61℃ |
| Power 125W |
AMD should halve power consumption in 45nm , or 200W will follow at 3 Ghz clock.
Intel's Nehalem is just around the corner.
Believe me.
Or look at this test below.

Saturday, July 05, 2008
Police officer: "Yes, it's the moon. Over."

 Control: "South Wales Police, what's your emergency?"
Control: "South Wales Police, what's your emergency?"
Caller: "It's not really. I just need to inform you that across the mountain there's a bright stationary object."
Control: "Right."
Caller: "If you've got a couple of minutes perhaps you could find out what it is? It's been there at least half an hour and it's still there."
Control: "It's been there for half an hour. Right. Is it actually on the mountain or in the sky?"
Caller: "It's in the air."
Control: "I will send someone up there now to check it out."
Caller: "OK."
After the police patrol car arrives, the script reveals the exchange between the control room and the police officer sent to the scene.
Control: "Alpha Zulu 20, this object in the sky, did anyone have a look at it?"
Officer: "Yes, it's the moon. Over."
Friday, July 04, 2008
Fat vs thin client computing
UK MOD to roll out 6000 terminals each month
The new system is being built by the Atlas consortium led by U.S. computer firm EDS and will eventually deliver 150,000 computer terminals at more than 2,000 locations, including Royal Navy warships.
BADHARDWARE verdict: Terminals? Mainframe empire strikes back.
By the way, EDS is not in delivery problems relating to MoD for the first time.
New unified computer system seems have been planned online for attack on Iran, that now might happen in the next 18 months, taking in account all EDS delays.
Thursday, July 03, 2008
Israel had conducted air operations over the Mediterranean that could simulate a strike on Iran.
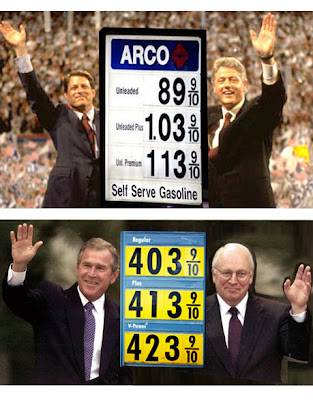
President Bush's tour to see the results of his disastrous presidency
Reifeiser file system developer has developmental disability
"This is complete and total nonsense," says Reiser's prosecutor, Paul Hora. "All of a sudden he's incompetent a week before he gets sentenced."
Wednesday, July 02, 2008
1 Exaflops by the year 2019
By that stage, though, competition between Europe, Japan and the U.S. for the supercomputing crown may no longer be an option. "We may have to cooperate at a global level to push past one petaflop," said Stevens.
AMD has stolen 2% of Intel's market in Q1 !!
AMD Intel war heats up.
"It will be an interesting second half," said Brookwood. "AMD has been trying hard to convince everyone that the dark clouds hanging over them for most of 2007 have blown away."